(Dependency Track, Best Practices) Introduction In May 2021 President of the USA Joe Biden has issued the Executive Order 14028 on “Improving the Nation’s Cybersecurity”. The document makes several demands on federal agencies concerning the implementation of Cybersecurity and identifies the security and integrity of the software supply chain as one vital claim.
Messages de Rogue Scholar
August, 2022 Authors: Daniel S. Katz, Tom Honeyman, Paula Andrea Martinez, Michelle Barker, Leyla Jael Castro, Neil Chue Hong, Morane Gruenpeter, Jennifer Harrow, Anna-Lena Lamprecht, Carlos Martinez-Ortiz, Fotis Psomopoulos Introduction This blog post describes the need for, the work towards, and the recent completion of version 1.0 of the FAIR Principles for Research Software (FAIR4RS Principles v1.0). It also briefly discusses the principles
August, 2022 Authors: Daniel S. Katz, Tom Honeyman, Paula Andrea Martinez, Michelle Barker, Leyla Jael Castro, Neil Chue Hong, Morane Gruenpeter, Jennifer Harrow, Anna-Lena Lamprecht, Carlos Martinez-Ortiz, Fotis Psomopoulos Introduction This blog post describes the need for, the work towards, and the recent completion of version 1.0 of the FAIR Principles for Research Software (FAIR4RS Principles v1.0). It also briefly discusses the

The first post on this blog was published on August 3, 2007 (Open access may become mandatory for NIH-funded research). This is post number 465, and in the past 15 years the blog has seen changes in technology and hosting location – but I wrote all posts (with the exception of a few guest posts). The overall theme remained unchanged: technology used in scholarly communication.

Slack is a wonderful tool for communicating and organising work in teams. Many academic groups are using the free version (since the pricing is simply incompatible with how we are funded). Slack has had a 10,000 message limit for free tier workspaces for many years but they recently changed it to a 90 day limit. This means any messages older than 90 days will no longer be visible.
In the last post, we used the qualtRics 1 package to import survey data directly from Qualtrics accounts.I often use Qualtrics for survey data collected via Amazon’s Mechanical Turk, which is an automated system that connects online respondents to paid surveys.However, sometimes those data are not super useful because the quality of the data is poor.In the anonymous, large-scale market of online survey respondents, the financial
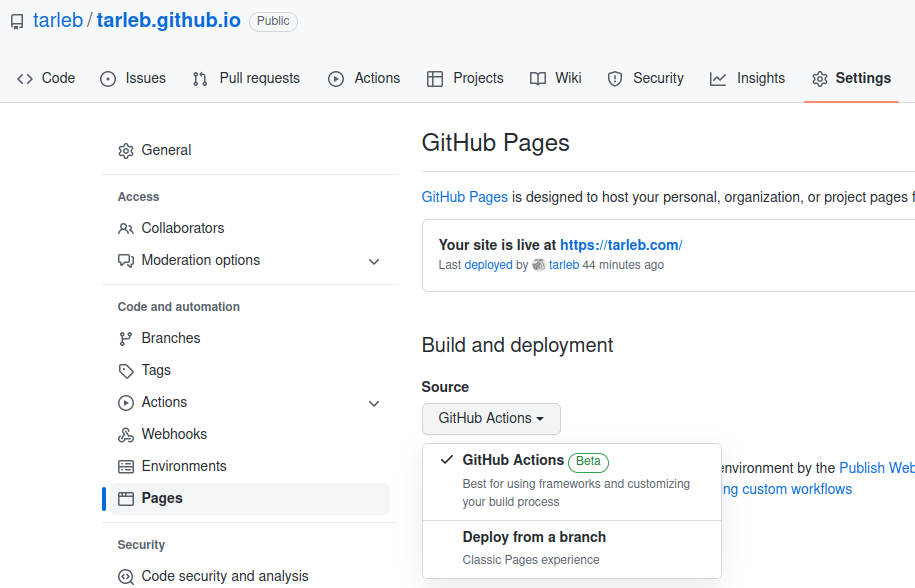
Quarto makes it very easy to publish a website via GitHub Pages: It is as simple as running quarto publish gh-pages. Here we explore a slightly different method that uses a GitHub Action to publish the website automatically every time it is updated. Classic GitHub Pages The classic way to publish a website via GitHub pages is to maintain a separate branch gh-pages.

Quarto makes it very easy to publish a website via GitHub Pages: It is as simple as running quarto publish gh-pages. Here we explore a slightly different method that uses a GitHub Action to publish the website automatically every time it is updated. Classic GitHub Pages The classic way to publish a website via GitHub pages is to maintain a separate branch gh-pages.

Since around this time last year, I have been working on creating a library of identification resources. Here, “identification resources” are identification keys, multi-access (matrix) keys, other works that can aid in the identification of species. The project is managed on GitHub: https://github.com/identification-resources.

I once saw a brilliant presentation about how simple data analysis can detect credit card fraud**. The presentation showed a pattern in how people use their credit cards. Given a large number of people who had been victims of credit card fraud, this pattern showed there was just 1 store in-particular where they had all used their cards. There was no observational evidence of someone at that store stealing card details.